Opinion
Lightning Network In A Class Of Its Own At Bitcoin 2024 Conference
Published
5 months agoon
By
admin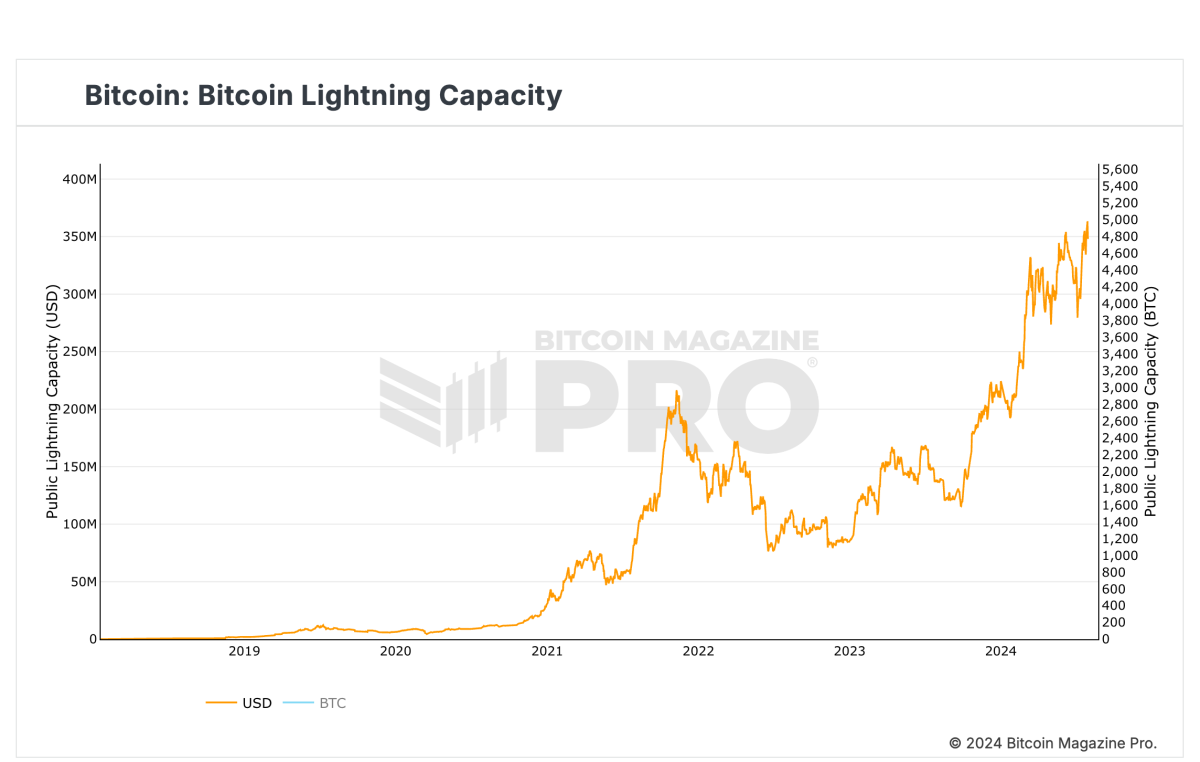
I was asked repeatedly throughout this year’s Bitcoin 2024 conference what my highlight of the moment was — what the signal was amongst the noise. As I returned from Nashville, it occurred to me that, each time, I could never answer the question satisfyingly.
In part, because I simply couldn’t keep up. The activity around the news desk and my support for those running the show left me with little time to focus on anything else. I can’t say I regret it. Anyone who gravitated around our livestream studio space during the week can attest to the energy surrounding it. The Bitcoin Magazine news desk was the veritable heartbeat of the conference.
Now that I’ve had time to collect my thoughts, I can confidently say what stood out most from the conference was the understated presence of the Lightning Network. In different times this would have been a concern but this felt different. It struck me that Lightning has not only arrived but has matured beyond what any other scaling layer can realistically claim.
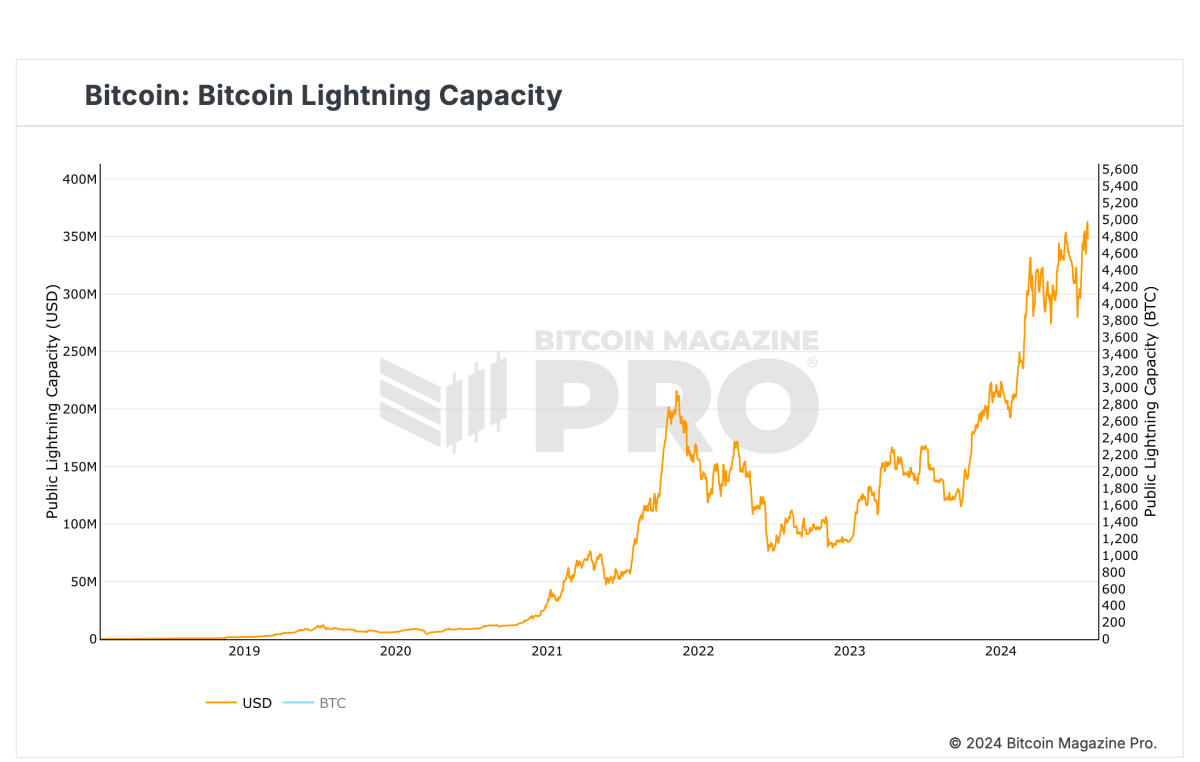
Largely unnoticed, the payment protocol has quietly inserted itself into every piece of major Bitcoin infrastructure. Most of the world’s leading exchanges now support it, with some running the largest nodes on the network. The dollar-denominated capacity of the network is at an all-time high, and every operator I spoke with this week confirmed its rapidly improving reliability.
Though it might have looked to the casual conference goer that Lightning had taken a back seat to other popular up-and-coming protocols, it was clear during the conference how vastly ahead it is from the rest of the field. While I was fortunate to meet many talented individuals working on this new generation of Bitcoin technical design, I left the event with more questions about their progress than when I arrived. Lightning, on the other hand, answered many concerns about its status and the road ahead.
Sights on settlements
A recurring narrative during the event was the protocol’s promises as a settlement network. Initially promoted as a retail payment solution, Lightning’s latest and biggest headways might be among businesses and institutions looking to satisfy liquidity needs. The vision, popularized notably by Jack Mallers at Strike, feels more concrete than ever, with infrastructure company Lightspark now at the forefront of these accomplishments. Last Thursday, on the Nakamoto stage, Lightspark’s co-founder Christian Catalini argued for Lightning’s favorable position as a bridge between companies and various financial institutions:
If you think about the challenge of moving value not just between a few countries but two hundred or more countries, every day, 24/7, with deep liquidity. There is only one asset, and that asset is bitcoin. It has regulatory clarity, it has on and off-ramps in pretty much every country around the globe. Now we can connect it all in an open way.
Lightspark’s recent announcement of its partnership with Latin America’s banking giant Nubank clearly outlines the potential for existing firms to modernize their infrastructure using the Lightning network.
Further strengthening the case of Lightning as a rail to connect the global economy, last week’s release of Lightning Labs’ Taproot Asset protocol introduces yet another opportunity for the scaling layer to establish itself as the dominant value transfer protocol on the internet. Before Lightning can come for VISA, it might have to start by displacing SWIFT.
Improving payments
On the payment front, the talk of the town in Nashville was the improvement in user experience brought about by the arrival of features like BOLT12.
Years in the making, the payment protocol offers an intuitive way for users to receive Lightning payments without relying on unreliable, expiring, invoices. It also paves a promising path toward improving users’ ability to receive payments offline, a major pain point of current implementations.
Introducing #TwelveCash, a simple way to share your bitcoin payment info with the world. pic.twitter.com/tynzAVEEEt
— Stephen DeLorme (@StephenDeLorme) July 18, 2024
BOLT12 achieves this through static, reusable, offers that do not compromise receiver privacy. Combined with other innovations like DNS payment instructions, it is now possible to create human-readable Bitcoin addresses (ex: alex@twelve.cash) that support different payment formats. Imagine using a single identifier to receive on-chain and Lightning payments regardless of your preferred standards. Twelve.cash, a standout project from this year’s conference hackathon, did a remarkable job highlighting the versatility of this technology, implementing “a simple way to share your bitcoin payment info with the world.”
Other forms of human-readable addresses have existed for some time using the LNURL format but the hope is for users to converge to more mature solutions. Long-time Lightning infrastructure provider Amboss also announced during the event a new Lightning wallet supporting a novel, multi-asset, payment system they’ve called “MIBAN”.
Fragmentation between standards and compatibility issues is anticipated in open and permissionless financial systems. Lightning is further than any alternative in terms of optimizing around these interoperability challenges to ensure seamless payment experiences.
BOLT12 is currently supported by leading wallets like Phoenix and ZEUS, and could land on the Strike app soon.
Following Bitcoin Park’s Lightning Summit around the same time last year, I remember feeling pretty disillusioned about the prospects of consumer Lightning apps. What a difference a year makes. While a fully non-custodial experience might always command a premium, new optimizations, and different security models are emerging that can meet retail users where they are.
Infrastructure at scale
This progress, at every level, would not be possible without the momentous efforts that have gone into infrastructure work over the last couple of years.
Lightspark, which supports Lightning integration for other industry giants like Coinbase and Bitso, is powered by Spiral’s Lightning Development Kit (LDK). Recently announced Alby Hub is also the first production wallet deployed using the LDK node library.
Keep in mind LDK has been in the works for almost four years now. Good things take time. Many people I spoke to during the conference expect the scope and quality of projects to be deployed using this toolkit to significantly accelerate.
Another signal of the evolving Lightning infrastructure came from the release during the week of Breez LDK’s new Liquid integration. This is a trend that is picking up pace and has been pioneered by Boltz’s swapping services. Used in wallet applications like Aqua, Liquid empowers developers to use the sidechain network’s cheap fees to settle transactions in and out of Lightning into L-BTC. While this involves custody tradeoffs, proponents argue it remains a superior option to fully custodial Lightning wallets.
Also in topic during the conference was the progress made at the Lightning Service Provider (LSP) specification level. As a result, the quality of service providers on the network has significantly increased. LSPs are used to provide infrastructure support and liquidity provision to companies wanting to connect to the Lightning Network.
Zeus’s founder Evan Kaloudis shared his company’s effort in this direction:
Since the legal uncertainty in the space arose following the arrest of the Samourai Wallet developers, we’ve doubled down and now have two different services that provide users with connectivity to the Lightning Network. We’ve also massively expanded the Olympus LSP userbase; we now are not only powering the ZEUS wallet, but we’ve now got integrations in a total of four different wallets, including a role as the default LSP in Mutiny Wallet.
Security is another area of the protocol seeing impressive growth. Spiral grantee Sean Gillian’s work on Validating Lightning Signer (VLS) will play a significant role in scaling this technology to power users. Allowing operators to leverage secure enclaves to protect hot signing keys and set spending policies will be required to onboard the next wave of institutional players.
In a panel I hosted Saturday afternoon called “Lightning for Institutions”, the protocol’s co-creator Tadge Dryja expressed strong interest in the development of more secure key management processes.
We’ve worked out how you can implement multi-signature support for Lightning nodes. We have done the math, we know it works. Now we have to work with everyone to get there.
It would not be an infrastructure section without mentioning the massive innovation around the Nostr protocol and its implications for Lightning. One of my favorite Pitchday projects at the conference was Flash, a new payment gateway platform that leverages Nostr for seamless integration of Lightning into any internet services or products. The consequences of using the Nostr messaging protocol as a bridge between Bitcoin applications are not yet fully appreciated. The Flash team has an incredible vision for it. Shoutout also to Justin from Shocknet who I met and is exploring many interesting ways to scale the Lightning protocol using Nostr’s magic sauce.
It’s time to stop fading Lightning.
Source link
You may like


Here’s why Stellar Price Could Go Parabolic Soon
Perp-Focused HyperLiquid Experiences Record $60M in USDC Net Outflows


Experts say these 3 altcoins will rally 3,000% soon, and XRP isn’t one of them


Robert Kiyosaki Hints At Economic Depression Ahead, What It Means For BTC?


BNB Steadies Above Support: Will Bullish Momentum Return?


Metaplanet makes largest Bitcoin bet, acquires nearly 620 BTC



Recently, BlackRock released an educational video explaining Bitcoin, which I thought was great—it’s amazing to see Bitcoin being discussed on such a massive platform. But, of course, Bitcoin X (Twitter) had a meltdown over one specific line in the video: “There is no guarantee that Bitcoin’s 21 million supply cap will not be changed.”
HealthRnager from Natural News claimed, “Bitcoin has become far too centralized, and now the wrong people largely control its algorithms. They are TELLING you in advance what they plan to do.”
Now, let me be clear: this is total nonsense. The controversy is overhyped, and the idea that BlackRock would—or even could—change bitcoin’s supply is laughable. The statement in their video is technically true, but it’s just a legal disclaimer. It doesn’t mean BlackRock is plotting to inflate bitcoin’s supply. And even if they were, they don’t have the power to pull it off.
Bitcoin’s 21 million cap is fundamental—it’s not up for debate. The entire Bitcoin ecosystem—miners, developers, and nodes—operates on this core principle. Without it, Bitcoin wouldn’t be Bitcoin. And while BlackRock is a financial giant and holds over 500,000 Bitcoin for its ETF, its influence over Bitcoin is practically nonexistent.
Bitcoin is a proof-of-work (PoW) system, not a proof-of-stake (PoS) system. It doesn’t matter how much bitcoin BlackRock owns; economic nodes hold the real power.
Let’s play devil’s advocate for a second. Say BlackRock tries to propose a protocol change to increase bitcoin’s supply. What happens? The vast network of nodes would simply reject it. Bitcoin’s history proves this. Remember Roger Ver and the Bitcoin Cash fork? He had significant influence and holdings, yet his version of bitcoin became irrelevant because the majority of economic actors didn’t follow him.
If Bitcoin could be controlled by a single entity like BlackRock, it would’ve failed a long time ago. The U.S. government, with its endless money printer, could easily acquire 10% of the supply if that’s all it took to control Bitcoin. But that’s not how Bitcoin works. Its decentralized nature ensures no single entity—no matter how powerful—can dictate its terms.
So, stop worrying about BlackRock “changing” Bitcoin. Their influence has hard limits. Even if they tried to push developers to change the protocol, nodes would reject it. Bitcoin’s decentralization is its greatest strength, and no one—not BlackRock, not Michael Saylor—can change that.
This article is a Take. Opinions expressed are entirely the author’s and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
Source link
Opinion
It’s Time to Admit It – There Are Only 2.1 Quadrillion Bitcoins
Published
2 days agoon
December 21, 2024By
admin
If the above statement offends you, you might not have read the Bitcoin source code.

https://x.com/pete_rizzo_/
Of course, I’m sure you’ve heard that there are 21 million bitcoin – and this is true, the Bitcoin protocol allows for only “21 million bitcoin” to be created, yet these larger denominations can be subdivided into 100 million sub-units each.
Call them whatever you want, there are only 2.1 quadrillion monetary units in the protocol.
This dollars and cents differential has long been the subject of debate – in the time of Satoshi, Bitcoin’s creator, the dual conventions, Bitcoin having both a bulk denomination, and a smaller unit, was not much of a concern. There were questions about whether the software would work at all, and bitcoin were so worthless, selling them in bulk was the only rational option.
Rehashing this debate is BIP 21Q, a proposal to the Bitcoin users authored by John Carvalho, founder of Synonym, creator of the Pubky social media platform, and a tenured contributor whose work dates back to the days of the influential Bitcoin-assets collective.
In short, the BIP proposes that network actors – the various wallets and exchanges – change how Bitcoin denominations are displayed, with the smallest unit of the protocol renamed “bitcoins,” as opposed to “satoshis,” as they have been commonly called.
Here are the specifics of the BIP:
Redefinition of the Unit:
- Internally, the smallest indivisible unit remains unchanged.
- Historically, 1 BTC = 100,000,000 base units. Under this proposal, “1 bitcoin” equals that smallest unit.
- What was previously referred to as “1 BTC” now corresponds to 100 million bitcoins under the new definition.
Terminology:
- The informal terms “satoshi” or “sat” are deprecated.
- All references, interfaces, and documentation SHOULD refer to the base integer unit simply as “bitcoin.”
Display and Formatting:
- Applications SHOULD present values as whole integers without decimals.
- Example:
- Old display: 0.00010000 BTC
- New display: 10000 BTC (or ₿10000)
Unsurprisingly, the debate around the BIP has been hostile. For one, it’s not a technical BIP, though this is not a requirement of the BIP process. Suffice to say, it’s perhaps the most general BIP that has been proposed under the BIP process to date, as it mainly deals with market conventions and user onboarding logic, not any changes to the software rules.
However, I have to say, I find the proposal compelling. Nik Hoffman, our News Editor, does not, preferring to stick to the market affirmative.
Yet, I think the proposal raises relevant questions: why should new users be forced to compute their Bitcoin balances using only decimals? Surely this has the adverse side effect of making commerce difficult – it’s simply antithetical to how people think and act today.
Also, in terms of savings, at an $100,000 BTC price, it isn’t exactly compelling to think you could be spending a whole year earning 1 BTC, though that may be.
Indeed, there have been various debates for all kinds of units – mBTC, uBTC – that play around with the dollars and cents convention, but Carvalho here is wisely skipping to the end, preferring just to rip the band-aid off. $1 would buy 1,000 bitcoins under his proposal.
What’s to like here, and I argued this during a Lugano debate on the topic in 2023, is that it keeps both the larger BTC denomination and the smaller unit, now bitcoins. They are both important, and serve different functions.
My argument then was that having a larger denomination like BTC (100 million bitcoins) is important. If there was no “BTC unit,” the press and financial media would be faced to reckon that “1 bitcoin” is still worth less than 1 cent.
How much mainstream coverage and interest do we think there would be? I’d bet not very much.
In this way, BIP 21Q is a best-of-both-worlds approach.
The financial world, press, and media can continue championing the meteoric rise in value of “BTC,” while everyday users can get rid of decimals and complex calculations, trading the only real Bitcoin unit guaranteed to exist in perpetuity.
This article is a Take. Opinions expressed are entirely the author’s and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
Source link
Bitcoin spot ETF
We Need In-Kind Redemptions For The Spot Bitcoin ETFs
Published
2 days agoon
December 21, 2024By
admin


On a recent episode of the Coinage podcast, guest SEC Commissioner Hester Peirce said that she is open to reconsidering in-kind redemptions for spot bitcoin ETFs.
(For those who aren’t familiar with the term “in-kind redemption,” it refers to the ability to withdraw the bitcoin you’ve purchased via an ETF into your own custody. In essence, it turns a bitcoin IOU into the real thing.)
BREAKING: SEC Commissioner Hester Peirce previews new pro-crypto changes coming to the SEC
ETF in-kind redemptions and ability for ETF issuers to begin staking likely done "early on"
Both ETFs now have more than $100B in AUM pic.twitter.com/g3jtbuBeWU
— Coinage (@coinage_media) December 20, 2024
This makes my heart happy, as bitcoin wasn’t designed to exist trapped within the wrappers of the old system. It was built to set us free from that system.
If Peirce can work with the incoming SEC Chair, Paul Atkins, to facilitate the approval of in-kind redemptions then the spot bitcoin ETFs can serve as some of the biggest on-ramps to Bitcoin, as Bitwise co-founder Hong Kim put it, as opposed to simply existing as speculation vehicles.
Bitcoin was born to exist in the wild. It wasn’t born to exist in a Wall Street zoo.
In-kind redemptions would allow the bitcoin currently trapped within the zoo the ability to return to its natural habitat.
This article is a Take. Opinions expressed are entirely the author’s and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
Source link

Here’s why Stellar Price Could Go Parabolic Soon

Perp-Focused HyperLiquid Experiences Record $60M in USDC Net Outflows

Experts say these 3 altcoins will rally 3,000% soon, and XRP isn’t one of them

Robert Kiyosaki Hints At Economic Depression Ahead, What It Means For BTC?

BNB Steadies Above Support: Will Bullish Momentum Return?

Metaplanet makes largest Bitcoin bet, acquires nearly 620 BTC

Tron’s Justin Sun Offloads 50% ETH Holdings, Ethereum Price Crash Imminent?

Investors bet on this $0.0013 token destined to leave Cardano and Shiba Inu behind

End of Altcoin Season? Glassnode Co-Founders Warn Alts in Danger of Lagging Behind After Last Week’s Correction

Can Pi Network Price Triple Before 2024 Ends?

XRP’s $5, $10 goals are trending, but this altcoin with 7,400% potential takes the spotlight

CryptoQuant Hails Binance Reserve Amid High Leverage Trading

Trump Picks Bo Hines to Lead Presidential Crypto Council

The introduction of Hydra could see Cardano surpass Ethereum with 100,000 TPS

Top 4 Altcoins to Hold Before 2025 Alt Season
182267361726451435

Why Did Trump Change His Mind on Bitcoin?

Top Crypto News Headlines of The Week

New U.S. president must bring clarity to crypto regulation, analyst says

Will XRP Price Defend $0.5 Support If SEC Decides to Appeal?

Bitcoin Open-Source Development Takes The Stage In Nashville

Ethereum, Solana touch key levels as Bitcoin spikes

Bitcoin 20% Surge In 3 Weeks Teases Record-Breaking Potential

Ethereum Crash A Buying Opportunity? This Whale Thinks So

Shiba Inu Price Slips 4% as 3500% Burn Rate Surge Fails to Halt Correction

Washington financial watchdog warns of scam involving fake crypto ‘professors’

‘Hamster Kombat’ Airdrop Delayed as Pre-Market Trading for Telegram Game Expands

Citigroup Executive Steps Down To Explore Crypto
Mostbet Güvenilir Mi – Casino Bonus 2024

NoOnes Bitcoin Philosophy: Everyone Eats
Trending

 3 months ago
3 months ago182267361726451435

 Donald Trump5 months ago
Donald Trump5 months agoWhy Did Trump Change His Mind on Bitcoin?

 24/7 Cryptocurrency News4 months ago
24/7 Cryptocurrency News4 months agoTop Crypto News Headlines of The Week

 News4 months ago
News4 months agoNew U.S. president must bring clarity to crypto regulation, analyst says

 Price analysis4 months ago
Price analysis4 months agoWill XRP Price Defend $0.5 Support If SEC Decides to Appeal?

 Opinion5 months ago
Opinion5 months agoBitcoin Open-Source Development Takes The Stage In Nashville

 Bitcoin5 months ago
Bitcoin5 months agoEthereum, Solana touch key levels as Bitcoin spikes

 Bitcoin5 months ago
Bitcoin5 months agoBitcoin 20% Surge In 3 Weeks Teases Record-Breaking Potential


