Crypto scam
Threat of fake job applications in crypto
Published
5 months agoon
By
admin
Suspected North Korean operatives are allegedly using fake job applications to infiltrate web3 projects, siphoning off millions and raising security concerns.
In the last few years, blockchain and web3 have been at the forefront of technological innovation. However, to paraphrase a quote, with great innovation comes great risk.
Recent revelations have uncovered a sophisticated scheme by operatives suspected to be affiliated with the Democratic People’s Republic of Korea to infiltrate the sector through fake job applications, raising alarms about the security and integrity of the industry.
Economic motives and cyber strategies
North Korea’s economy has been severely crippled by international sanctions, limiting its access to crucial resources, restricting trade opportunities, and hindering its ability to engage in global financial transactions.
In response, the regime has employed various methods to circumvent these sanctions, including illicit shipping practices, smuggling, and tunneling, as well as using front companies and foreign banks to conduct transactions indirectly.
However, one of the DPRK’s most unconventional methods of raising revenue is its reported use of a sophisticated cybercrime warfare program that allegedly conducts cyberattacks on financial institutions, crypto exchanges, and other targets.
The crypto industry has been one of the biggest victims of this rogue state’s alleged cyber operations, with a TRM report from earlier in the year indicating crypto lost at least $600 million to North Korea in 2023 alone.
In total, the report stated that North Korea was responsible for an eye-watering $3 billion worth of crypto stolen since 2017.
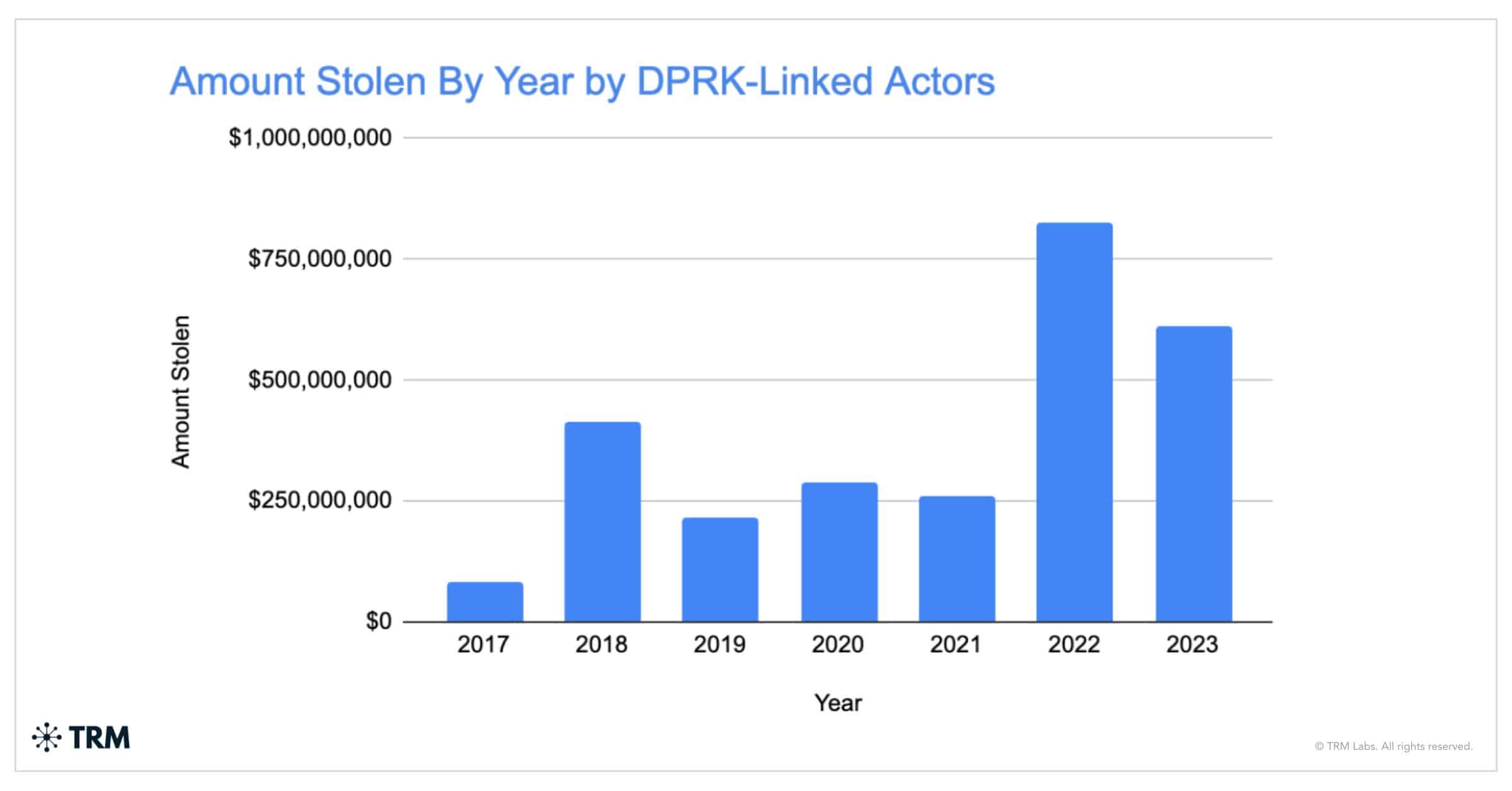
With crypto seemingly a soft and lucrative target, reports have emerged of DPRK-linked actors tightening the screw by infiltrating the industry using fake job applications.
Once hired, these operatives are in a better position to steal and siphon off funds to support North Korea’s nuclear weapons program and circumvent the global financial restrictions imposed on it.
The modus operandi: fake job applications
Going by stories in the media and information from government agencies, it seems DPRK operatives have perfected the art of deception, crafting fake identities and resumes to secure remote jobs in crypto and blockchain companies worldwide.
An Axios story from May 2024 highlighted how North Korean IT specialists were gaming American hiring practices to infiltrate the country’s tech space.
Axios said the North Korean agents use forged documents and fake identities, often masking their true locations with VPNs. Additionally, the story claimed that these would-be bad actors primarily target sensitive roles in the blockchain sector, including developers, IT specialists, and security analysts.
300 companies affected by fake remote job application scam
The scale of this deception is vast, with the U.S. Justice Department recently revealing that more than 300 U.S. companies were duped into hiring North Koreans through a massive remote work scam.
These scammers not only filled positions in the blockchain and web3 space but also allegedly attempted to penetrate more secure and sensitive areas, including government agencies.
According to the Justice Department, the North Korean operatives used stolen American identities to pose as domestic technology professionals, with the infiltration generating millions of dollars in revenue for their beleaguered country.
Interestingly, one of the orchestrators of the scheme was an Arizona woman, Christina Marie Chapman, who allegedly facilitated the placement of these workers by creating a network of so-called “laptop farms” in the U.S.
These setups reportedly allowed the job scammers to appear as though they were working within the United States, thereby deceiving numerous businesses, including several Fortune 500 companies.
Notable incidents and investigations
Several high-profile cases have shown how these North Korea-linked agents infiltrated the crypto industry, exploited vulnerabilities, and engaged in fraudulent activities.
Cybersecurity experts like ZachXBT have provided insights into these operations through detailed analyses on social media. Below, we look at a few of them.
Case 1: Light Fury’s $300K transfer
ZachXBT recently spotlighted an incident involving an alleged North Korean IT worker using the alias “Light Fury.” Operating under the fake name Gary Lee, ZachXBT claimed Light Fury transferred over $300,000 from his public Ethereum Name Service (ENS) address, lightfury.eth, to Kim Sang Man, a name which is on the Office of Foreign Assets Control (OFAC) sanctions list.
Light Fury’s digital footprint includes a GitHub account, which shows him as a senior smart contract engineer who has made more than 120 contributions to various projects in 2024 alone.
Case 2: the Munchables hack
The Munchables hack from March 2024 serves as another case study showing the importance of thorough vetting and background checks for key positions in crypto projects.
This incident involved the hiring of four developers, suspected to be the same person from North Korea, who were tasked with creating the project’s smart contracts.
The fake team was linked to the $62.5 million hack of the GameFi project hosted on the Blast layer-2 network.
The operatives, with GitHub usernames such as NelsonMurua913, Werewolves0493, BrightDragon0719, and Super1114, apparently displayed coordinated efforts by recommending each other for jobs, transferring payments to the same exchange deposit addresses, and funding each other’s wallets.
Additionally, ZachXBT said they frequently used similar payment addresses and exchange deposit addresses, which indicated a tightly-knit operation.
The theft happened because Munchables initially used an upgradeable proxy contract that was controlled by the suspected North Koreans who had inveigled themselves into the team, rather than the Munchables contract itself.
This setup provided the infiltrators with significant control over the project’s smart contract. They exploited this control to manipulate the smart contract to assign themselves a balance of 1 million Ethereum.
Although the contract was later upgraded to a more secure version, the storage slots manipulated by the alleged North Korean operatives remained unchanged.
They reportedly waited until enough ETH had been deposited in the contract to make their attack worthwhile. When the time was right, they transferred approximately $62.5 million worth of ETH into their wallets.
Fortunately, the story had a happy ending. After investigations revealed the former developers’ roles in the hack, the rest of the Munchables team engaged them in intense negotiations, following which the bad actors agreed to return the stolen funds.
$97m has been secured in a multisig by Blast core contributors. Took an incredible lift in the background but I’m grateful the ex munchables dev opted to return all funds in the end without any ransom required. @_munchables_ and protocols integrating with it like @juice_finance…
— Pacman | Blur + Blast (@PacmanBlur) March 27, 2024
Case 3: Holy Pengy’s hostile governance attacks
Governance attacks have also been a tactic employed by these fake job applicants. One such alleged perpetrator is Holy Pengy. ZachXBT claims that name is an alias for Alex Chon, an infiltrator allied to the DPRK.
When a community member alerted users about a governance attack on the Indexed Finance treasury, which held $36,000 in DAI and approximately $48,000 in NDX, ZachXBT linked the attack to Chon.
According to the on-chain investigator, Chon, whose GitHub profile features a Pudgy Penguins avatar, regularly changed his username and had been reportedly fired from at least two different positions for suspicious behavior.
In an earlier message to ZachXBT, Chon, under the Pengy alias, described himself as a senior full-stack engineer specializing in frontend and solidity. He claimed he was interested in ZachXBT’s project and wanted to join his team.
An address linked to him was identified as being behind both the Indexed Finance governance attack and an earlier one against Relevant, a web3 news sharing and discussion platform.
Case 4: Suspicious activity in Starlay Finance
In February 2024, Starlay Finance faced a serious security breach impacting its liquidity pool on the Acala Network. This incident led to unauthorized withdrawals, sparking significant concern within the crypto community.
The lending platform attributed the breach to “abnormal behavior” in its liquidity index.
Security Incident Report: Anomaly in USDC Pool and Exploitation
Executive Summary:
This report details a critical security incident within the Starlay protocol’s USDC lending pool on the Acala EVM platform. An exploit was identified and executed due to abnormal behavior in the… https://t.co/8Q3od5g6Rc— Starlay Finance🚀 (@starlay_fi) February 9, 2024
However, following the exploit, a crypto analyst using the X handle @McBiblets, raised concerns regarding the Starlay Finance development team.
I’ve looked into the @starlay_fi incident and there is something extremely suspicious about their dev team, David and Kevin
I would not be surprised if they were responsible for the recent attack and my intuition is making me think they could be DPRK affiliated
Here’s why 🧵
— McBiblets (@mcbiblets) March 16, 2024
As can be seen in the X thread above, McBiblets was particularly concerned with two individuals, “David” and “Kevin.” The analyst uncovered unusual patterns in their activities and contributions to the project’s GitHub.
According to them, David, using the alias Wolfwarrier14, and Kevin, identified as devstar, appeared to share connections with other GitHub accounts like silverstargh and TopDevBeast53.
As such, McBiblets concluded that those similarities, coupled with the Treasury Department’s warnings about DPRK-affiliated workers, suggested the Starley Finance job may have been a coordinated effort by a small group of North Korean linked infiltrators to exploit the crypto project.
Implications for the blockchain and web3 sector
The seeming proliferation of suspected DPRK agents in key jobs poses significant risks to the blockchain and web3 sector. These risks are not just financial but also involve potential data breaches, intellectual property theft, and sabotage.
For instance, operatives could potentially implant malicious code within blockchain projects, compromising the security and functionality of entire networks.
Crypto companies now face the challenge of rebuilding trust and credibility in their hiring processes. The financial implications are also severe, with projects potentially losing millions to fraudulent activities.
Furthermore, the U.S. government has indicated that funds funneled through these operations often end up supporting North Korea’s nuclear ambitions, further complicating the geopolitical landscape.
For that reason, the community must prioritize stringent vetting processes and better security measures to safeguard against such deceptive job-hunting tactics.
It is important for there to be enhanced vigilance and collaboration across the sector to thwart these malicious activities and protect the integrity of the burgeoning blockchain and crypto ecosystem.
Source link
You may like

Most Layer 2 solutions are still struggling with scalability


Here’s why Stellar Price Could Go Parabolic Soon
Perp-Focused HyperLiquid Experiences Record $60M in USDC Net Outflows


Experts say these 3 altcoins will rally 3,000% soon, and XRP isn’t one of them


Robert Kiyosaki Hints At Economic Depression Ahead, What It Means For BTC?


BNB Steadies Above Support: Will Bullish Momentum Return?
Blockchain
Crypto fakes on X nearly doubled, reaching over 300 accounts daily
Published
2 weeks agoon
December 10, 2024By
admin

Bad actors keep ramping up crypto scams, with impersonation accounts surging to over 300 a day, according to blockchain analysts.
Crypto scams on X are once again rising fast, with major accounts hijacked to promote fake tokens. Victims have already lost millions, and experts are warning users to stay alert.
Analysts at blockchain firm Scam Sniffer warned in an X post on Dec. 10 that starting this week, daily impersonation accounts surged by 87%, jumping to over 300 compared to the November average of 160. The spike increases the risk for users as scammers continue to exploit high-profile accounts to push fraudulent schemes.
🚨 SCAM ALERT: Surge in X Impersonations 📈
Our monitoring system detected a significant increase in crypto fake accounts this week, with daily numbers reaching 300+ (vs. Nov avg. 160) 📊
⚠️ Two victims lost over $3M recently from clicking malicious links/signing transactions… pic.twitter.com/eGhG1GPX0r
— Scam Sniffer | Web3 Anti-Scam (@realScamSniffer) December 10, 2024
The analysts note that in one recent case alone, two victims lost over $3 million worth of crypto by interacting with malicious links and signing transactions linked to fake accounts. As crypto.news reported earlier, the scams are particularly prevalent on Solana (SOL), where compromised accounts, including those of major entities like Yahoo News UK, Lenovo India, and Money Control, have been used to push a scam meme coin called HACKED.
Blockchain sleuth ZachXBT, who has been tracking these scams, recently issued a warning to the crypto community, advising users to be extra cautious. “So far, it seems the scammers may have lost money, as the market cap of the HACKED token is a modest $67K, and top traders have barely made $1K,” ZachXBT noted.
The compromised X accounts appear to have been connected to the same malicious site or application. As a precaution, ZachXBT recommends that users revoke any access permissions to unfamiliar sites or apps.
The latest incident follows a series of similar scams, including the recent use of Kylian Mbappé’s account to promote a fake MBAPPE meme coin. Earlier in September, hackers also targeted family members of U.S. president-elect Donald Trump in a scam involving the fake World Liberty Financial coin.
Source link
Crypto scam
Why HAWK Memecoin Crashed from $500M to $60M in Minutes
Published
3 weeks agoon
December 5, 2024By
admin

Hailey Welch, an influencer on social media, launched her own memecoin, Hawk Tuah, on Dec. 4. The cryptocurrency crashed from $500 million to $60 million in just 20 minutes post-launch.
Hailey Welch, commonly known as the Hawk Tuah Girl on the internet, launched her new memecoin of the same name, $HAWK, on Solana on Dec. 4. The coin quickly took off, garnering a market cap of about $500 million, which then crashed to nearly $60 million, all within 20 minutes of launch. The news was further confirmed by Solana (SOL) on X.
Who is Hawk tuah girl?
Welch first rose to fame as the “Hawk tuah girl” after a video of her went viral, making a comical onomatopoeic sound of spitting took over social media earlier this year. With the meme, Welch soon progressed from working a minimum wage job to finding herself in an internet meme culture. Building on this viral moment, Welch launched the HAWK token.
Rise and fall of HAWK token
The massive drop of almost 88% in the HAWK token has reignited the discussion on the high volatility of memecoins in the cryptocurrency community. Some crypto users believe the token was initially built for rug pulling, a cryptocurrency scam in which developers withdraw liquidity or suddenly abandon a project, resulting in the token’s price plummeting.
According to content generated by the community on X, the Hawk token’s supply was allegedly “sniped” shortly after launch. This refers to instances where early investors or bots snatch up large amounts of tokens, leaving the broader community with less access and exposing them to risks. These are often warning signs of the health of the project as it shows few people own the token. However, not all holders have sold their HAWKs, as posted by a user, ZeusLFG, reflecting a strong optimism for the token.
At the time of writing, the token’s trading volume has risen exponentially by 951.67%, as per CoinMarketCap. While the debate goes on, Hawk Token remains under close observation, with members of the community demanding additional disclosures to confirm these claims and keep a close eye on this project.
Source link
24/7 Cryptocurrency News
Pro Gamer Linked to $3.5M Meme Coin Scam: ZachXBT
Published
4 weeks agoon
November 28, 2024By
admin
The crypto market has become the center of attention, with the Bitcoin price aiming at the $100k mark. However, another incident is also gaining investors’ attention these days. A famous crypto investigator, ZachXBT made a major crypto scam finding, linking a pro gamer to a $3.5M meme coin scam. More importantly, these scams were also linked to major celebrity social media account hacks, scam promotions, and much more.
At one point, the crypto industry had earned a name for itself among the biggest finance entities, with $3.31T in global market capitalization. However, the rising crypto scams, theft, and laundering are concerning. Even Changpeng Zhao showed disappointment in memecoin and the rising scams.
ZachXBT Unveils $3.5M MemeCoin Scam and the Culprit
In 2024, the crypto market faced many wallet hacks, rug pull scams, and many other concerning scams. However, celebrity account hacks and the promotion of cryptocurrency-related scams were the most frequent.
Considering the rising case, a popular crypto investigator, ZachXBT, analyzed nine celebrity account hacks and the involved meme coins. He concluded that there is a connection between all these hacks. More importantly, he claimed that a pro-Fortnite gamer known by the name Serpent is the mastermind behind this.
ZachXBT linked this pro gamer in the $3.5M meme coin scam, confirming that he used multiple Pump.Fun memecoin and pump and dump tactics to make millions. Surprisingly, the biggest connection was the Serpent’s ERROR project wallet, which interacted with every social media hacker’s wallets directly or indirectly.
1/ An investigation into how the threat actor Serpent went from a pro Fortnite player to helping steal $3.5M via meme coin scams launched from 9+ account compromises on X & IG and gambling the proceeds away at online casinos. https://t.co/zR6QtuQW8a pic.twitter.com/Y8ovnEnQgj
— ZachXBT (@zachxbt) November 27, 2024
Serpent is known as a pro gamer and blockchain security analyst. He is even the founder of the Sentinel, which is a threat mitigation system but new reports link him with the scam, making it a big controversy. More importantly, he scammed $3.5M and gambled them away in online casinos. The controversy grew as Serpent deleted many of his X posts right after ZachXBT’s claims.
Breaking Down The Serpent’s Crypto Scam
In a detailed X post, ZachXBT revealed his finding to the crypto community, which explained the memecoin scams of more than $3.5M after the scammer compromised various celebrity social media accounts. It includes the account hacks of McDonald’s, Usher, Kabosu Owner, Andy Ayrey, Wiz Khalifa, SPX 6900, etc X (Twitter) and Instagram.


McDonald’s Instagram hack was among the first hacks of the year, where the scammer promoted a memecoin called GRIMACE and earned more than $690k with the pump and dump tactics. This happened on August 21, and the person shifted the funds to two main crypto wallets. The crypto scammer transferred 101.5 SOL to two addresses on September 3 and deployed the SCHRADER token. Interestingly, this token was promoted during the Actor Dean Norris X account hack.
Further, on September 6, the scammer processed Mcdonald’s ATO to a casino deposit address with the beginning address as B2fw. This same account transferred 110 Sol to two new wallet addresses on September 12 and sniped the meme coins which was used during the Usher crypto hack. The same B2fw wallet transferred 4868 SOL to casino deposit address ECb5v, which is connected to Andy Ayrey and the Enoshima Aquarium hack on October 15. Within the same day, 84 SOLs were transferred to ECb5v.
Even the popular AI bot Truth Terminal owner’s X account got hacked on October 29, which stayed compromised for days. In that period, 6 memecoins were promoted on his account. All these involved a common 3GVUs wallet, and the same wallet transferred 169 SOL to Ecb5vs on October 30. However, this is just the mid, the list goes on for others.
Bottom Line
Meme-themed cryptocurrencies gained investors attention in 2024, where many offered heavy gains, mainly the Solana memecoins. As a result, millions of Solana-based meme tokens were launched this year on Pump. Fun, but many were misused for crypto scams. With his recent investigation, ZachXBT has revealed the person behind the $3.5M meme coins scam. The scams also involved hacking celebrity accounts and promoting tokens to boost their price and dumping them all. This way, the scammer or alleged pro-Fortnite gamer Serpent made heavy returns, but others were left with losses.
Pooja Khardia
With a deep-seated passion for reading and five years of experience in content writing, Pooja is now focused on crafting trending content about cryptocurrency market.
As a dedicated crypto journalist, Pooja is constantly seeking out trending topics and informative statistics to create compelling pieces for crypto enthusiasts. Staying abreast of the latest trends and advancements in the field is an integral part of her daily routine, fueling a commitment to delivering timely and insightful coverage
Disclaimer: The presented content may include the personal opinion of the author and is subject to market condition. Do your market research before investing in cryptocurrencies. The author or the publication does not hold any responsibility for your personal financial loss.
Source link

Most Layer 2 solutions are still struggling with scalability

Here’s why Stellar Price Could Go Parabolic Soon

Perp-Focused HyperLiquid Experiences Record $60M in USDC Net Outflows

Experts say these 3 altcoins will rally 3,000% soon, and XRP isn’t one of them

Robert Kiyosaki Hints At Economic Depression Ahead, What It Means For BTC?

BNB Steadies Above Support: Will Bullish Momentum Return?

Metaplanet makes largest Bitcoin bet, acquires nearly 620 BTC

Tron’s Justin Sun Offloads 50% ETH Holdings, Ethereum Price Crash Imminent?

Investors bet on this $0.0013 token destined to leave Cardano and Shiba Inu behind

End of Altcoin Season? Glassnode Co-Founders Warn Alts in Danger of Lagging Behind After Last Week’s Correction

Can Pi Network Price Triple Before 2024 Ends?

XRP’s $5, $10 goals are trending, but this altcoin with 7,400% potential takes the spotlight

CryptoQuant Hails Binance Reserve Amid High Leverage Trading

Trump Picks Bo Hines to Lead Presidential Crypto Council

The introduction of Hydra could see Cardano surpass Ethereum with 100,000 TPS
182267361726451435

Why Did Trump Change His Mind on Bitcoin?

Top Crypto News Headlines of The Week

New U.S. president must bring clarity to crypto regulation, analyst says

Will XRP Price Defend $0.5 Support If SEC Decides to Appeal?

Bitcoin Open-Source Development Takes The Stage In Nashville

Ethereum, Solana touch key levels as Bitcoin spikes

Bitcoin 20% Surge In 3 Weeks Teases Record-Breaking Potential

Ethereum Crash A Buying Opportunity? This Whale Thinks So

Shiba Inu Price Slips 4% as 3500% Burn Rate Surge Fails to Halt Correction

Washington financial watchdog warns of scam involving fake crypto ‘professors’

‘Hamster Kombat’ Airdrop Delayed as Pre-Market Trading for Telegram Game Expands

Citigroup Executive Steps Down To Explore Crypto
Mostbet Güvenilir Mi – Casino Bonus 2024

NoOnes Bitcoin Philosophy: Everyone Eats
Trending

 3 months ago
3 months ago182267361726451435

 Donald Trump5 months ago
Donald Trump5 months agoWhy Did Trump Change His Mind on Bitcoin?

 24/7 Cryptocurrency News4 months ago
24/7 Cryptocurrency News4 months agoTop Crypto News Headlines of The Week

 News4 months ago
News4 months agoNew U.S. president must bring clarity to crypto regulation, analyst says

 Price analysis4 months ago
Price analysis4 months agoWill XRP Price Defend $0.5 Support If SEC Decides to Appeal?

 Opinion5 months ago
Opinion5 months agoBitcoin Open-Source Development Takes The Stage In Nashville

 Bitcoin5 months ago
Bitcoin5 months agoEthereum, Solana touch key levels as Bitcoin spikes

 Bitcoin5 months ago
Bitcoin5 months agoBitcoin 20% Surge In 3 Weeks Teases Record-Breaking Potential



✓ Share: