Bounty
WazirX co-founder announces bounty program to recover funds
Published
5 months agoon
By
admin
WazirX co-founder Nischal Shetty has announced a bounty program to help the exchange recover or freeze funds stolen in the exchange’s recent hack.
As reported earlier this week by crypto.news, the exploit saw losses amounting to more than $234 million in several cryptocurrencies.
WazirX Team is actively working on next steps.
1. We’re preparing a bounty program to help us freeze/recover the stolen assets
2. Further discussions on continuous tracing of fund movements, we’re in touch with a few teams that claim to be experts at this.
3. We’ve informed all…— Nischal (Shardeum) 🔼 (@NischalShetty) July 20, 2024
According to an X post from Shetty, the bounty program was launched earlier today. WazirX had initially proposed a $11.5m total bounty for recovering the assets, but the co-founder later said it was updated to $23m after the intercession of crypto security sleuth ZachXBT.
Shetty said the bounty program was a way for the exchange to get assistance from the crypto community in its quest to recover the money stolen in the July 18 cyberattack.
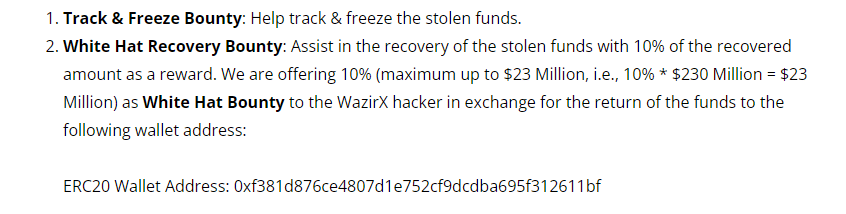
According to WazirX’s official blog, the program consists of two initiatives. The first is a track and freeze bounty, aimed at helping locate and freeze the stolen assets. The second is a white hat recovery bounty, offering a reward of 10% of the recovered amount to those who assist in retrieving the funds.
The exchange has publicly shared an ERC20 wallet address for the return of the stolen funds as can be seen below.
The crypto community on X has raised concerns over how “sluggish” measures taken to recover the funds have been, with some speculating on how the hack happened. Plenty of guesses have leaned towards the Lazarus Group’s involvement.
$10M bounty means nothing if it is indeed Lazarus Group as they are not going to just hand over the funds or be located and held legally accountable.
5% is lower than 10%+ industry standard
— ZachXBT (@zachxbt) July 21, 2024
Although the exchange is optimistic some of the funds can be recovered, blockchain analytics firm Arkham confirmed the hacker sold $102m worth of SHIB, which was part of the funds stolen.
Speculation on WazirX exploit method
An X user gave a breakdown on how the hack might have happened, insinuating that Shetty and the security team at WazirX were “sleeping while all these happened.”
Allow me to elaborate this WazirX Hack.
1. Attacker changed the contract which defines how the transactions are carried out. ( how the hell your key holders upgrade without cross checking the file)
2. When your key holder 1 signed first USDT transaction ,the attacker got 1st…
— Engineer Xplains (@engineer_inside) July 21, 2024
The X user believes the hacker modified the contract defining transaction procedures without detection. It’s reported that the attacker then captured signatures from three separate keyholders during failed transactions.
These signatures were subsequently used to create a test transaction that met Laminal’s approval criteria, paving the way for larger unauthorized transfers.
Shetty disagreed with the allegations, insisting Liminal’s security measures verify transaction correctness and checks for whitelisted addresses before signing. Furthermore, he went on to say Liminal only signs transactions initiated within its own system, not external ones, regardless of other signatures.
WazirX co-founder said the exchange is now awaiting Liminal’s detailed report on the incident, as well as forensic analysis of the three WazirX devices involved.
Source link
You may like


Robert Kiyosaki Hints At Economic Depression Ahead, What It Means For BTC?


BNB Steadies Above Support: Will Bullish Momentum Return?


Metaplanet makes largest Bitcoin bet, acquires nearly 620 BTC


Tron’s Justin Sun Offloads 50% ETH Holdings, Ethereum Price Crash Imminent?


Investors bet on this $0.0013 token destined to leave Cardano and Shiba Inu behind


End of Altcoin Season? Glassnode Co-Founders Warn Alts in Danger of Lagging Behind After Last Week’s Correction

Robert Kiyosaki Hints At Economic Depression Ahead, What It Means For BTC?

BNB Steadies Above Support: Will Bullish Momentum Return?

Metaplanet makes largest Bitcoin bet, acquires nearly 620 BTC

Tron’s Justin Sun Offloads 50% ETH Holdings, Ethereum Price Crash Imminent?

Investors bet on this $0.0013 token destined to leave Cardano and Shiba Inu behind

End of Altcoin Season? Glassnode Co-Founders Warn Alts in Danger of Lagging Behind After Last Week’s Correction

Can Pi Network Price Triple Before 2024 Ends?

XRP’s $5, $10 goals are trending, but this altcoin with 7,400% potential takes the spotlight

CryptoQuant Hails Binance Reserve Amid High Leverage Trading

Trump Picks Bo Hines to Lead Presidential Crypto Council

The introduction of Hydra could see Cardano surpass Ethereum with 100,000 TPS

Top 4 Altcoins to Hold Before 2025 Alt Season

DeFi Protocol Usual’s Surge Catapults Hashnote’s Tokenized Treasury Over BlackRock’s BUIDL

DOGE & SHIB holders embrace Lightchain AI for its growth and unique sports-crypto vision

Will Shiba Inu Price Hold Critical Support Amid Market Volatility?
182267361726451435

Why Did Trump Change His Mind on Bitcoin?

Top Crypto News Headlines of The Week

New U.S. president must bring clarity to crypto regulation, analyst says

Will XRP Price Defend $0.5 Support If SEC Decides to Appeal?

Bitcoin Open-Source Development Takes The Stage In Nashville

Ethereum, Solana touch key levels as Bitcoin spikes

Bitcoin 20% Surge In 3 Weeks Teases Record-Breaking Potential

Ethereum Crash A Buying Opportunity? This Whale Thinks So

Shiba Inu Price Slips 4% as 3500% Burn Rate Surge Fails to Halt Correction

Washington financial watchdog warns of scam involving fake crypto ‘professors’

‘Hamster Kombat’ Airdrop Delayed as Pre-Market Trading for Telegram Game Expands

Citigroup Executive Steps Down To Explore Crypto
Mostbet Güvenilir Mi – Casino Bonus 2024

NoOnes Bitcoin Philosophy: Everyone Eats
Trending

 3 months ago
3 months ago182267361726451435

 Donald Trump5 months ago
Donald Trump5 months agoWhy Did Trump Change His Mind on Bitcoin?

 24/7 Cryptocurrency News4 months ago
24/7 Cryptocurrency News4 months agoTop Crypto News Headlines of The Week

 News4 months ago
News4 months agoNew U.S. president must bring clarity to crypto regulation, analyst says

 Price analysis4 months ago
Price analysis4 months agoWill XRP Price Defend $0.5 Support If SEC Decides to Appeal?

 Opinion5 months ago
Opinion5 months agoBitcoin Open-Source Development Takes The Stage In Nashville

 Bitcoin5 months ago
Bitcoin5 months agoEthereum, Solana touch key levels as Bitcoin spikes

 Bitcoin5 months ago
Bitcoin5 months agoBitcoin 20% Surge In 3 Weeks Teases Record-Breaking Potential


